FIDO has been around for quite a while and is best known for hardware tokens like Yubikey. There has been limited adoption, primarily in enterprise contexts where it can be mandated or by security-sensitive individuals. FIDO has, from the start, been looking into performing authentication directly on-device or using the mobile phone as an authenticator device. Despite these specifications being around for a while, this FIDO flavour has barely been adopted.
What did FIDO announce?
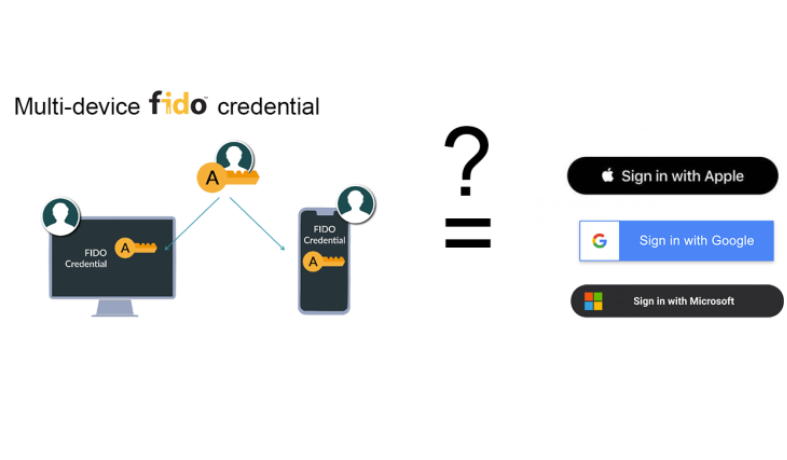
FIDO announced multi-device FIDO credentials, or Passkeys as Apple, Google, and Microsoft call them. These allow you to share FIDO credentials across multiple devices and recover them, e.g., after phone loss. Although this looks very nice from a user perspective, it comes with a nasty catch. The promise that keys will be synced or recovered through the cloud essentially means that one of FIDO’s initial claims to fame – secure key storage – is no longer valid. FIDO relies (relied on?) on dedicated hardware tokens or an on-device TPM (trusted platform module – secure hardware) to guarantee that the private key cannot be extracted and never leaves the device.
FIDO used to have a strong coupling between the secure hardware and the on-device biometrics: only after submitting a correct biometric sample the secure hardware could use the FIDO credentials once to sign a challenge.
But with the FIDO credentials no longer residing in secure hardware (as this does not allow for extracting keys), this strong coupling with the on-device biometrics is gone as well. Furthermore, it is not because two devices are linked with the same Apple/Google/Microsoft account that these contain the same set of biometrics, e.g., your personal phone and a tablet at home, which is shared with your family.
This is what the FIDO Alliance states on its own website in the FAQ on security:
How does FIDO Authentication make users safer on the web?
Unlike current password-based authentication models that have proven vulnerable to mass-scale attacks and fraud, FIDO authentication credentials are never shared or stored in centralized databases. FIDO credentials are known and maintained only by the user’s own device. All that is ever stored by the service provider are the public keys paired to the user’s device where the private keys are stored. For additional security and privacy, biometrics used in FIDO Authentication never leave the device. This security model eliminates the risks of phishing, all forms of password theft and replay attacks. [...]
What are the consequences for users?
All the above will also reinforce the grip of Apple, Google, and Microsoft on its users’ accounts. These companies will happily accept your keys. To what extent you’ll be able to control it and protect yourself from prying government eyes, remains to be seen.
It is also improbable that Apple, Google, Microsoft, etc. will allow third-party FIDO authenticators on its devices. How cross-platform sync will take place also remains to be seen, as all three players tend to consider its own accounts as the-one-and-only. Will your Chrome browser on your Microsoft device live in the Google universe, while your iPhone has all the Apple-linked credentials?
Ultimately, when users can sync and recover their FIDO keys through their Apple/Google/Microsoft credentials, the security of the FIDO keys also boils down to this. This begs the question for website or app owners, why bother with FIDO and not simply implement a login with your Apple/Google/Microsoft account button?
How are we different?
At nextAuth, we do not believe in putting all your credentials in the hands of big tech. For high security, credentials should be linked to a device and locked to the current set of biometrics (i.e. invalidated when a new biometric sample is added). nextAuth allows you to do all that, and moreover couple multiple devices to the same user. Each device comes with its own credentials that are securely stored in hardware and coupled with the on-device biometrics.
That’s only one of the ways nextAuth sets itself apart from FIDO. Click on the button below and discover how we are different from FIDO.